|
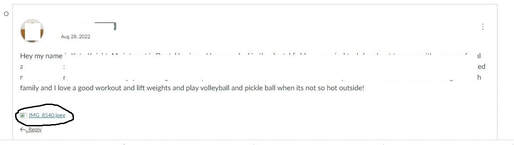
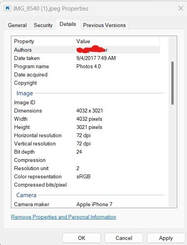
Part of the 21st century skills required of everyone – but especially of public facing figures including educators – is actively securing as much privacy as you can in a post-privacy world. These tips should help and hopefully mitigate some risks of the profession and its exposure. Good luck! Reasons for Paying Attention to Cyber Privacy Hygiene From doxxing to personal attacks to online automated or bot harassment to the exploitation of accidentally leaked personal details, educators can become targets of trolls, 'watcher' groups, irate former students, and others. This post will share some VERY BASIC low effort actions and tips you can do without going paranoid to lower your privacy vulnerability, and better protect your personal information from tracking, stalking, and 'dirty tricks' while and after teaching. Why do you need to be able to secure your privacy as an educator in 2023 with more rigor than an average citizen’s practice of ‘post-privacy’ cyber-hygiene? The two links below illustrate two variations of a personal grudge. 8chan/8kun style message boards and sites on the Dark Web have shared step-by-step guides and tools to carry out reputation attacks such as these with more than a few requests for teachers, professors, and others in education as retaliation for disciplinary action, perceived personal dislike, or bad grades/performance reviews. But reputation attacks aren’t the only risk. A google search for articles about lists of faculty listed as ‘radical’ left or right (with sometimes shared personal information) yields posts with calls for harassment or even violence. "I'm a Professor, which isn't usually a dangerous job" (Doerfleur et al, 2021) further provides examples of risks specifically for higher education faculty and researchers. Web 2.0 approach: Teacher framed by students for watching porn. Web 3.0 approach: Deep fake porn nearly ruined my life. The tips below are minimal and basic, but can still work to reduce risk even against the Web 3.0 newer style privacy violations of plug and play online identity impersonation, social engineering, and A.I. assisted deep fakes (video and audio). Tip 1 - Sharing the Screen When sharing screen (Zoom, Webex, etc) with students live, in online office hour meetings, demonstrating a quick google search for an answer or website visit, or recording in video, double check (or change how much of the screen shows) that no embarrassing or personal open browser tabs are showing, even if just for a moment -- and close your ‘file explorer’ so that you are not allowing any file names to be visible on your drives or the cloud. It may take a second to toggle between tabs during a screen share, but a video or screen capture can reveal/scrape information about your computer and your files that can lead to ideas and the use of tools for probing for more information. Also, be careful of what shows in the open apps bottom corner when sharing screens (what virus checker, other applications installed, etc). The risk of the digital or automated version of shoulder surfing exists for both embarrassment as well as privacy probing. Tip 2 - Profile Pictures Do NOT use the same profile photos in personal social media, in your faculty google email or zoom/Webex profile, and/or for posting or posting comments in social media or news groups. The temptation to use the same beautiful headshot is real. However, as, public safety and military personnel and their families have long known/been told, there are risks of posting or ‘being tagged’ to social media and being targeted. This is increasingly extending to faculty posting to social media groups and certain uses of general media or even posting on established news and media sites or conferences. A quick search on an image search engine (google image search, tineye, etc) can connect the dots between same teaching, professional, personal, and social media identity. A quick use of increasingly available cheap or free A.I. image combiners/aggregators or ‘create’ engines similar in effect to popular app Lensa, for example, or for worse effect, porn deep fake embedding apps or deep fake other uses, can quickly mesh and get search engines optimized with your identity. Using different pictures does not eliminate this risk, but does increase the difficulty of anyone trying to ‘connect your dots.’ Tip 3: Attaching Images or Files Attaching images or documents vs metadata. When you share a picture or file (including a document, docx, or PDF) by attaching to email directly sent to student or others, or even shared in a google directory, or shared as an attachment in Canvas in-box or in a Canvas discussion group thread* meta-information often stays intact. For example, a shared docx for an assignment in a shared google folder or a meme or intro/icebreaker picture innocently attached in a Canvas discussion group can have information embedded such as type of phone or camera, location, original version of document date, name, etc. Caption: Canvas Discussion board “Intro” Assignment where student attached image
Tip 4: Bluetooth on Your Phone/Tablet Turn off Bluetooth on phones and smartwatches when you are in class. A very cheap app on a phone or laptop can be used to try to connect to your device via Bluetooth and if your phone or smartwatch has older/not been freshly updated for security, someone in 10 feet range in class or near your office can sometimes get information or access. Tip 5: Write/Research/Advocate for Targeted/Adversarial Populations If you are a participant citizen, work with targeted populations (domestic or international, e.g. ‘closeted’ groups or refugees), work as or work with journalists, host events that can be considered polarizing, engage in public scholarship (“sharing research with audiences outside of academic settings”) or advocate, write about, or research politically targeted demographics or adversarial topics such as hackers, dis/misinformation, extremist/fundamentalist groups, take a look at the EFF guide to securely and safely attending protests, conferences, browsing risky sites, etc. This will help you keep good cyber privacy hygiene. For context, Alexandra Ketchum (as shared on the Association of Internet Researchers) covers some ideas/risk related topics in her book, Engage in Public Scholarship. Special thanks to Miguel Fernandez, who holds a Masters in National Security and Intelligence Studies which required active privacy measures and counter-measures as part of his studies and research and is a participant in The AOIR [unofficial] Risky Research Working Group and a member of DRONERESPONDERS’ Nationwide CUAS [Counter-drone] Working Group.
0 Comments
Your comment will be posted after it is approved.
Leave a Reply. |
Categories
All
Author
Awesome people who want to help you do awesome stuff in the classroom! Join the conversation here or in our Facebook Group: CGCC Center for Teaching, Learning, and Assessment Archives
October 2023
|
TOPICS |
SUPPORT HoursMonday - Thursday
8am - 4pm Friday - Out for Summer |
|
© Chandler-Gilbert Community College, 2024.








 RSS Feed
RSS Feed
